ID Card News

Visitor Mangement Security: HID EasyLobby® Secure!
Does your organization deal with numerous visitors every day? Without proper management solutions, your company is actively putting itself at risk due to a lack of security. If you need...
Visitor Mangement Security: HID EasyLobby® Secure!
Does your organization deal with numerous visitors every day? Without proper management solutions, your company is actively putting itself at risk due to a lack of security. If you need...
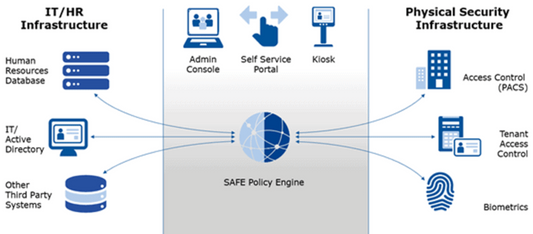
Access Control Solutions: HID SAFE™ Enterprise!
If your enterprise is searching for the simplest and most efficient way to effectively manage your access control, then the HID SAFE™ Enterprise is the ID software solution for you!...
Access Control Solutions: HID SAFE™ Enterprise!
If your enterprise is searching for the simplest and most efficient way to effectively manage your access control, then the HID SAFE™ Enterprise is the ID software solution for you!...
Visitor Management Solutions: HID WorkforceID™!
An industry-leading visitor management system, the HID WorkforceID™ Visitor Management solution can integrate seamlessly into any organization's visitor workflow experience. With the ability to customize and organize the workflow based...
Visitor Management Solutions: HID WorkforceID™!
An industry-leading visitor management system, the HID WorkforceID™ Visitor Management solution can integrate seamlessly into any organization's visitor workflow experience. With the ability to customize and organize the workflow based...

Hacking and 2FA - Free White Paper
A lot of people think PKI using SmartCards and Certificate Authorities is the only way to go. It works, but it is complex and requires significant IT resources to maintain. ...
Hacking and 2FA - Free White Paper
A lot of people think PKI using SmartCards and Certificate Authorities is the only way to go. It works, but it is complex and requires significant IT resources to maintain. ...

6 ways your passwords are stolen
If you lose your password to a criminal, your entire existence can be re-written, compromised, duplicated, and used against you.
6 ways your passwords are stolen
If you lose your password to a criminal, your entire existence can be re-written, compromised, duplicated, and used against you.

How do I protect my computer from hackers?
There are steps you can take to protect your information. Your ID card can be the key.
How do I protect my computer from hackers?
There are steps you can take to protect your information. Your ID card can be the key.
