ID Card News

Should I replace my ID Card Printer?
Great question! As a rule of thumb... if you use a Card Printer multiple times per week and you get anywhere between 3 to 5 years out it, you are...
Should I replace my ID Card Printer?
Great question! As a rule of thumb... if you use a Card Printer multiple times per week and you get anywhere between 3 to 5 years out it, you are...
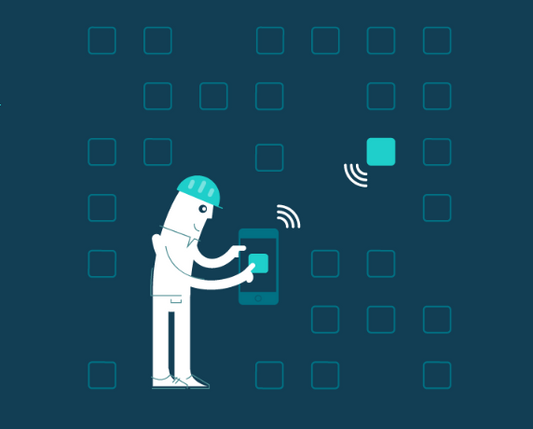
What is RTLS?
RTLS is one of the fasted growing technologies in the Internet of Things (IoT). You can have correct location information on your assets, in seconds. No more blind searching!
What is RTLS?
RTLS is one of the fasted growing technologies in the Internet of Things (IoT). You can have correct location information on your assets, in seconds. No more blind searching!

What is Cards-as-a-Service?
Cards as a Service is the new way to get ID cards fast, and efficiently. Outsource the hassle of printing while maintaining control of your design and database.
What is Cards-as-a-Service?
Cards as a Service is the new way to get ID cards fast, and efficiently. Outsource the hassle of printing while maintaining control of your design and database.

Buying an ID Printing Solution Without Expert A...
Avoid the nasty online purchasing surprise of "That's not what I wanted !" We can help. An expert is a quick phone call away.
Buying an ID Printing Solution Without Expert A...
Avoid the nasty online purchasing surprise of "That's not what I wanted !" We can help. An expert is a quick phone call away.
Giving Back - Pancake Breakfast !
Spending time in the community, giving back to schools and non-profit institutions, is something we do at IDEXPERTS®.
Giving Back - Pancake Breakfast !
Spending time in the community, giving back to schools and non-profit institutions, is something we do at IDEXPERTS®.

What are RFID Wristbands used for?
RFID Wristbands provide a fast and secure way to correctly identify the user, and grant or deny access based on the permission level they have.
What are RFID Wristbands used for?
RFID Wristbands provide a fast and secure way to correctly identify the user, and grant or deny access based on the permission level they have.
